Block XMLRPC and WP-LOGIN abuse with Cloudflare
Anyone running a website built on WordPress will have no doubt come across bots trying to access wp-login.php and xmlrpc.php for malicious means.
As long as you are using a strong username and password the chances of these bots being able to gain access to your website via a cracked password are slim but they can cause other problems such as overloading your website and causing you to get a telling off from your web host….not us obviously, we are far too kind for that.
Many people try and stop these bot attacks by using a security plugin but this can still cause problems as a lot of security plugins can be overwhelmed by a large number of these bot attacks, especially if you are running your website on a budget hosting account.
In our experience the best way to stop these bots in their tracks is to cut them off before they even reach your web server and in this guide we will show you how to achieve just that by using a free Cloudflare account.
Step 1
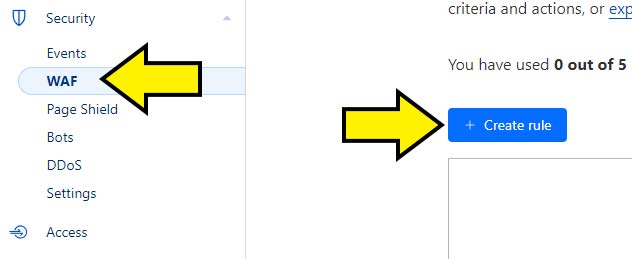
If you don’t already have one, create a free Cloudflare account and follow the initial setup steps. When you’ve done that log into your Cloudflare account and click on Security > WAF > Create Rule
Step 2
The first rule we will create is to present a “Managed Challenge” to anyone trying to access the WordPress admin area of our website. These Managed Challenges are great because they cause very little inconvenience to genuine (human!) users but they stop bots in their tracks.
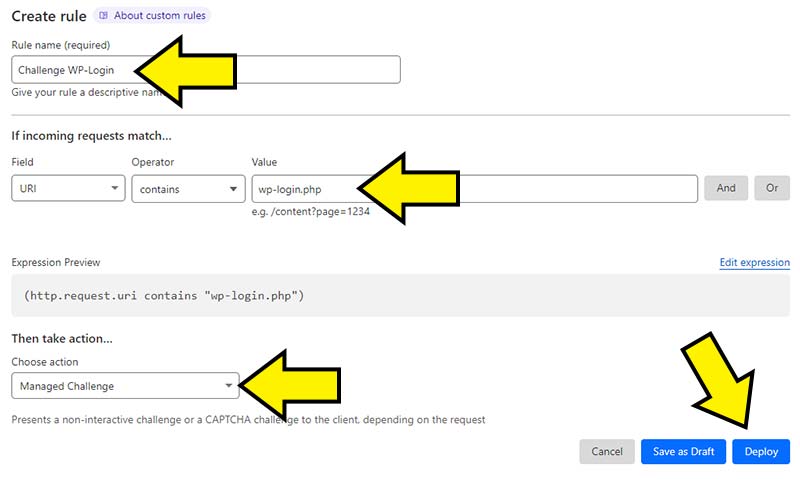
As shown in the screenshot below, first off give your new rule a name and then enter the following:
Field = URI
Operator = Contains
Value = wp-login.php
Under the “Then take action” text select “Managed Challenge” from the drop down menu. Finally click on the blue “Deploy” button.
Give it a few minutes for the rule to be deployed and then try and access your WordPress admin page. If you’ve got everything set up correctly you should very briefly see a screen like the following prior to your admin login page loading normally:

Step 3
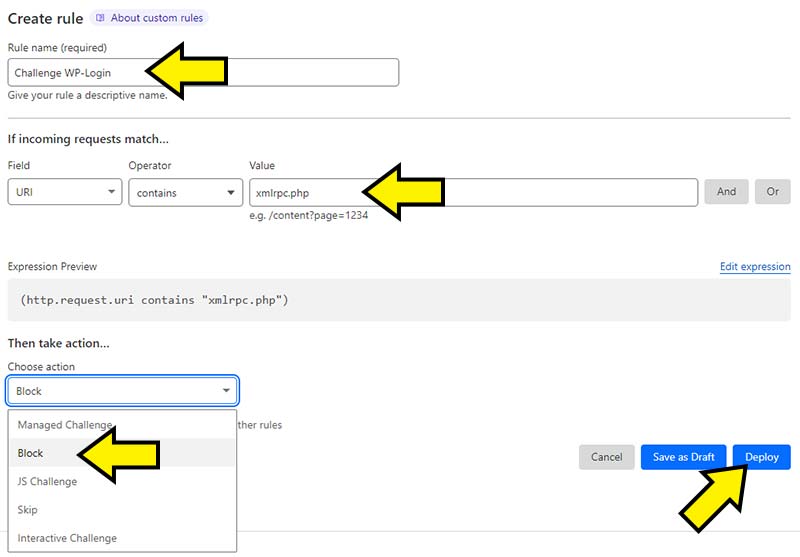
Now that we’ve got our login page protected we can move onto handling the xmlrpc.php abuse. In our experience the xmlrpc.php file is abused just as often, if not more than wp-login.php and the best thing to do IF your website doesn’t use the file is to simply block access to it. To do that head back to the rule deploy page and create a new rule with the following:
Field = URI
Operator = Contains
Value = xmlrpc.php
Under the “Take action” heading select “Block” and then deploy your new rule.
After doing this head back into your WordPress admin area and have a quick look around to see if everything looks fine. If it does then the chances are you don’t have any plugins using xmlrpc.php and you are safe to leave access to the file disabled. Some plugins do however still use this legacy file (looking at you JetPack!) and if this is the case then blocking the file globally wont work so you may need to get creative.
For example, we know that a lot of attacks come from countries such as Russia and China so you could use the “And” selector to add a country code in there to only apply the rule to certain countries. For example:
IF URI contains wp-login.php AND country code = RU OR CN THEN block
It would also be a good idea to add a global “Allow” rule for your own IP address (if your broadband provider provides you with a static IP) and also the IP of the server hosting your website.
You can do this on the same “WAF” page in Cloudflare by clicking on the “Tools” tab and by adding the IP addresses you want to allow as shown in the image below. If you are unsure what your local IP address is then you can find it here. You can also find out the IP address of your web server by asking your web host.
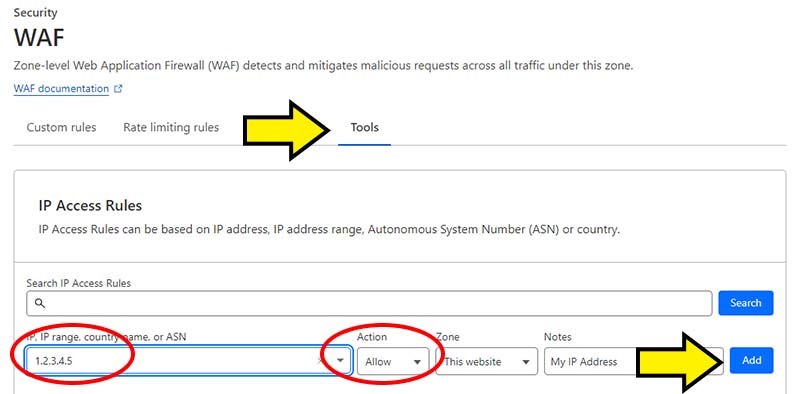
You can create up to 5 firewall rules on the free Cloudflare plan so have a play around with them to see what works for you. If, for example, you run a small coffee shop located in the UK and you’ve been having bot problems you could use the firewall rules to present a managed challenge to any website visitor NOT from the UK. The only limit is your imagination so give it a try and say BYE BYE BOTS!
